Welcome to Reputation America!
Have you found yourself the victim of a digital attack on your reputation? It can be a scary situation – after all, when negative, harmful, or false information is posted about you on the Internet, it can have devastating effects. And the longer this information stays online, the more it can affect your personal and professional life.
Whether you want to take down false reviews, outdated data, video mentions, or articles about you or your company, we'll get it done. If you are ready to take control of your online reputation, Reputation America is here to expertly and legally remove damaging content.




Guaranteed confidentiality, anonymity, and we write out the KPIs in the contract.
Lifetime guarantee If the negative information reappears again, we will delete it at our own expense.
Only legal methods Negotiation and social engineering - no hacking or threats.
Restore your privacy, repair your reputation, and reach a new level of control over your digital footprint. It's time to manage your reputation before your reputation manages you.





What Can You Do
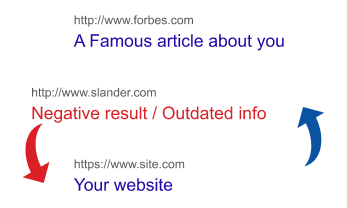
Deindex
The link leading to harmful information disappears from the search engine, but the content remains on the site



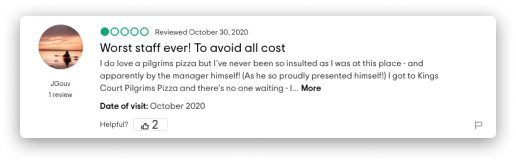
Information Removal
The unwanted information is deleted from the internet via negotiations



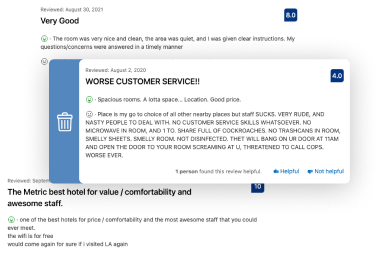
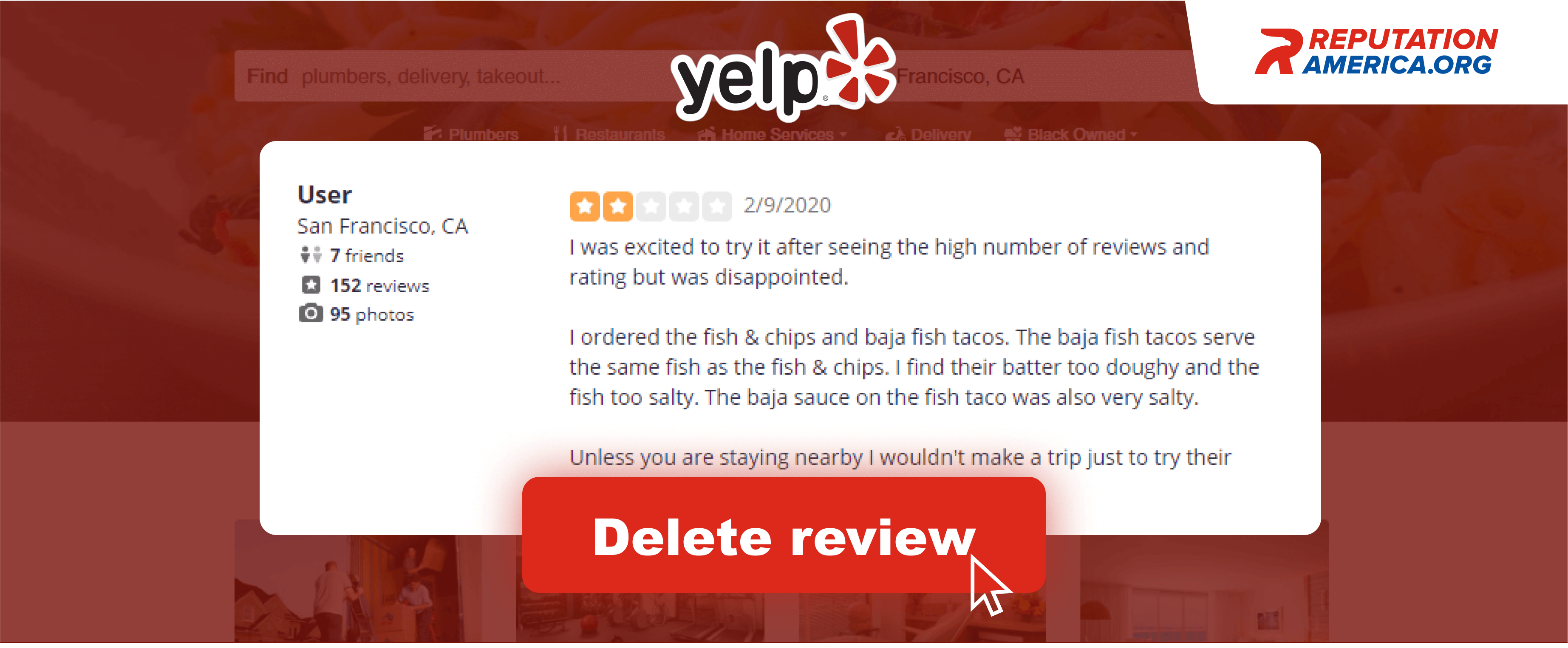
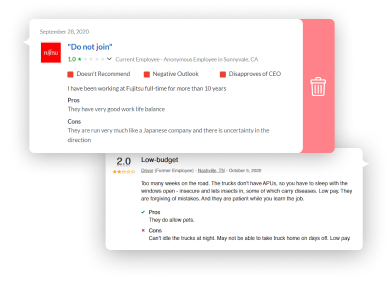
Reviews removal from former employees
Follow the best practices for dealing with bad reviews and manage to get them removed

You have a chance to improve your online presence.
Will you take it?
How it works
Analysis
We analyze the situation and find the best solutions to solve the problem. We provide you with exact terms and prices for each link.
Contract
We define the statement of work and sign a contract.
Removal Process
We will delete information using legal methods and without any risks for you.
Renewed Reputation
Clean reputation, negative content removed.

Resources
Read about free methods of information removal and hot lifehacks to preserve reputation. Cases and anti-cases. Useful and working content.